Published on 21st April 2020
Dear colleagues,
Due to the threat of a targeted cyberattack on healthcare infrastructures in the Czech Republic, which may also affect our infrastructure, we are publishing basic guidelines from the CSIRT-CUNI security team.
According to their statement, the anticipated attack vector is phishing + infected attachments and it is likely already in progress.
Current information about this attack can be found here:
https://www.irozhlas.cz/veda-technologie/koronavirus-coviper-narodni-urad-pro-kybernetickou-a-informacni-bezpecnost_2004181017_pj
How to remove CoViper Malware - virus removal instructions (updated)
Basic information has been adapted from the CSIRT-CUNI team, adjusted to the faculty conditions, and highlighted sections are as follows:
Optimal steps for reporting phishing attacks or reasonable suspicions are as follows:
- Consult your IT administrator to rule out false alarms and follow their recommendations (if immediate danger is present, decide on your own).
- Report the phishing email in Gmail (or similar action in other email clients if supported):
- Open the message.
- Next to the Reply button
 click on the options icon
click on the options icon  .
. - Click Report phishing.
- If you mistakenly marked the email as phishing, follow step 2 and click Report that it is not phishing in step c).
- Forward the email to CIT administrators at scam@natur.cuni.cz
- Move the message to the junk/spam folder or delete it (if it hasn’t already been done by marking it as phishing).
Similar campaigns are continuously happening on a smaller scale, and the CIT administrators are addressing these incidents.
Do not panic and do not spread suspicious e-mails further, except to the recipients mentioned above.
No one is authorized to ask you to send your system access credentials.
If you make a mistake and fall for a phishing attempt, immediately change the passwords for your accounts and inform the CIT administrators at scam@natur.cuni.cz
We are in contact with the security teams of CESNET and ÚVT UK, who are "defending" the perimeter, and we use additional internal data traffic monitoring tools, which increase the resilience of our systems against suspected activities. Your indispensable role in protecting the ICT infrastructure is to secure your devices against misuse, as outlined in OD4/2016.
Thank you for your cooperation
Have a nice day
Milan Richter and the CIT administrators
The following information has been taken from the CSIRT-CUNI team
Dangerous emails
All incoming faculty emails are checked by Google – antispam and antivirus. Another antivirus should be running on the computer where you read emails. However, this does not mean they are safe and nothing can go wrong.
The recipient of the email – a person – can ignore, turn off, or cleverly bypass all machine protections, checks, and security. Therefore, attackers focus on the person. They send an email in which they try to manipulate the recipient into doing what the computer will not do: revealing their password, turning off the computer's security, or opening an infected attachment. They send such emails to hundreds of thousands of addresses at once. It's cheap, and from the number of people sent, a few will certainly fall for it.
What could happen?
If a person reveals their email password, the attacker gains access to their correspondence, personal address book with names and addresses of others. They can read their emails and get the passwords to social media accounts – Facebook, Twitter, Instagram – and take them over. They can use the account to send out more fraudulent emails or send a large amount of unwanted advertising (spam). In such cases, the faculty's email server (organization) ends up on a blacklist of spammers, and the emails of everyone from the faculty will start landing in the spam folder. The entire faculty could then face email problems, usually for two weeks.
If a person opens an infected attachment, they open a path for the attacker into their computer and also to all the documents on servers that they have access to. The biggest danger today is the introduction of ransomware – a program that encrypts documents on the recipient’s computer and on servers so that they are unreadable. And for decrypting them, they demand a ransom. In the worst-case scenario, ransomware can paralyze the operations of an entire organization (as seen in the case of the hospital in Benešov).
Won't a firewall, antivirus, etc., protect me?
Every day, new variants of viruses and fraudulent emails emerge. Antivirus programs need to learn to recognize them. They learn quickly, but it still takes several hours before they can identify a new type of virus. When an attacker writes a new version of a fraudulent email and attaches a new type of virus, it's possible that the spam filter will let such an email through to the inbox. And when the recipient tries to open the attachment, the antivirus program won't intervene because it doesn't yet know the virus. It's dangerous when an attacker times the distribution of a new virus deliberately for early morning hours on Monday, so that by the start of the workday, the emails are already in the inboxes, and antivirus programs haven't reacted yet. We call this "dangerous Monday." This situation rarely occurs, but it does happen. That's why one must always (not just on Mondays) be cautious. Despite all technical measures, the user is the last line of defense for their computer.
Phishing
Phishing (the name comes from a distortion of the word "fishing") refers to fraudulent emails that manipulate the recipient into entering their email password (or even a credit card number) on a fake website linked from the email. Or they may even directly ask for it to be sent in a reply email.
Example:

This hypothetical phishing example is very easy to identify:
- By the sender's address – our faculty/university doesn't use the domain @webmaster.cz
- Using the informal "ty" form is not customary here
- Though it's in Czech, it contains several errors
- Suspicious signature
The link to the page you're supposed to click on is hidden. This is possible in HTML-format emails. You can find out where it really leads by hovering your mouse cursor over the link (without clicking!) and waiting for a moment:
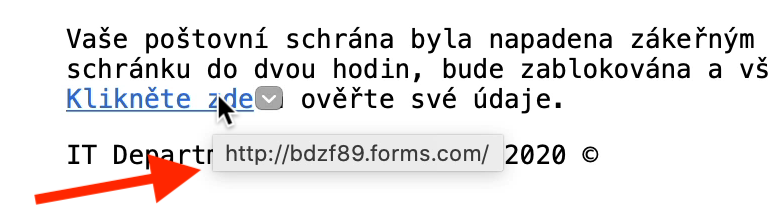
In webmail, the link will appear at the bottom of the window:
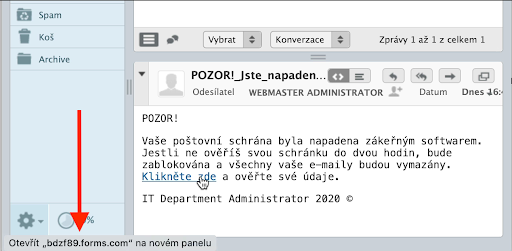
You can see that it leads to a foreign organization's server – another suspicious detail.
What could appear if someone still clicks the link:
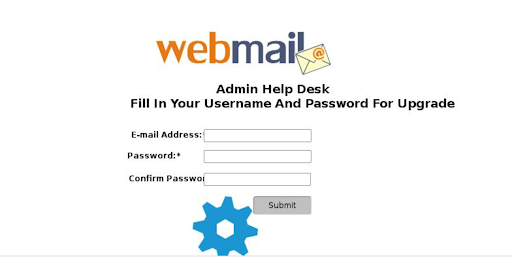
At first glance, what's suspicious on this page:
- You have never seen it before
- It doesn't have the organization's (university's) logo or name
It's just a clear scam.
However, a fake page may appear that closely imitates the real one:
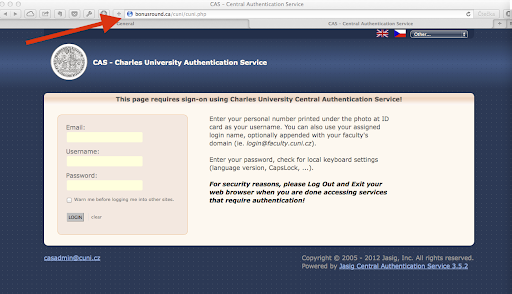
You probably visit the page cas.cuni.cz often, and the fake page shown above is very similar to it.
However, what you should check before entering your password anywhere is the URL of the page at the top: bonusround.ca/cuni/cuni.php.
The page is on the domain bonusround.ca, and that is not a university domain. The university domain ends with cuni.cz. Although the URL ends with /cuni/cuni.php and 'cuni' is part of the university domain, that is just to confuse you. In reality, this is a fake imitation of the cas.cuni.cz page, hosted on a server outside the university network. By trying to log in, you'll reveal your password. The login will fail, but you might then be redirected to the legitimate page, where the second attempt might succeed — but that should not reassure you.
Scammers may also try to trick you into clicking on a link and filling out a form with something else. For example, in 2020, the current “I found a secret document about the coronavirus on the World Health Organization's website - hurry, download it and read it before they remove it!”
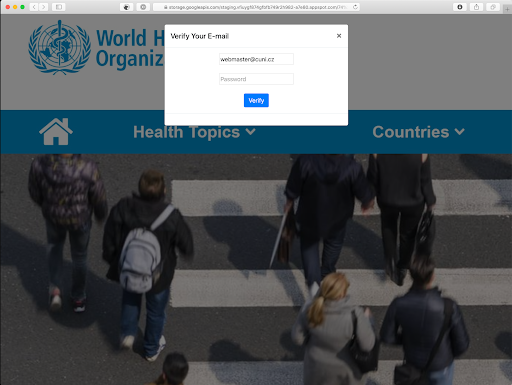
And again, a form to enter a username and password. For which account? Work email, private email, Office365...? If the frightened email recipient starts unsuccessfully trying one password after another, all the better for the attacker.
What to do if you fall for phishing?
First of all — everyone makes mistakes, and no one will penalize you for it. What is important is that you realize it and act quickly to prevent damage.
You must:
- inform CIT that your password has been compromised
- change the compromised password as soon as possible
CIT can temporarily block your account (to prevent the attacker from accessing your data and to stop the account from being misused — see above: What could happen — they will check if this has already occurred and help you set a new password).
Infected Attachments
Infected files may arrive in an email as an attachment, or there might be a link to download them from the email. The motivation to open the file could be the same as with phishing:
- threat, e.g. “this is your last warning to pay the debt before execution, details about the payment in the attached invoice”
- irresistible offer, e.g. “I found your profile on a social network, I really like you and would like to meet you, here are some of my photos”
- time pressure, e.g. “your email has won a lottery of 2,000,000 pounds, fill out the attached form and claim your prize within one hour, or we will give it to another winner”
- pretending to be an authority, e.g. “The EU Regional Development Commission asks you to fill out a simple questionnaire”
Usually, the fraudulent email will contain several of these elements at once.
Signs that an attachment may be dangerous:
- you don't know the sender and they have no reason to email you (e.g. you're not an accountant, so why would someone send you an invoice?)
- the file attachment has two extensions, e.g. “invoice.jpg.exe” — the “exe” extension means it's a program that could be infected, but the “.jpg” extension is just masking the program as a harmless image file
- the file has a different icon than the file type usually has (e.g. at first glance the attachment looks like a .docx file with a Word document icon, but upon closer inspection, you'll find the .exe extension at the end)
- the file is encrypted (usually with a .zip extension), and the password is in the body of the email. Even though it says the attachment is encrypted for security reasons, it's encrypted just so that the mail server's antivirus cannot check it.
Scams
For completeness, in addition to phishing and the transport of infected files, emails are used for a whole range of other scams. For example:
Payment Instructions for Foreign Transfers
The danger is that this is an attack targeted at a specific employee. The attacker finds a “supervisor - subordinate” pair, such as the director of a department or the head of finance. Impersonating the superior, the attacker then sends an email to the subordinate requesting the initiation of a payment order to transfer a large sum to a foreign account. They use various manipulative techniques ("urgent," "as soon as possible," "today," etc.). The return address of the fraudulent email correctly shows the superior's name and sometimes even the correct email address.
If you encounter this:
- Do not send any money without further verification (in person, by phone, not by email!) - follow internal processes and do not be manipulated into violating them!
- Do not worry that the employee's ("supervisor's") email has been compromised - in all known cases, the attacker only spoofed the return address, and they have not actually accessed the employee's email.
Extortion Emails
An extortionist threatens to publish a video recorded by the victim’s computer webcam. They demand payment in Bitcoin. To add weight to the threat:
- they spoof the sender address to match the victim's own email address
- they may include the victim's password to their computer (sometimes)
If you encounter this:
- Be sure that the hacker has not gained access to your computer. The attacker just sent out the email as spam, hoping that a small fraction of recipients will panic and actually pay.
- If they included a password in the email, you might have used it previously in a registration on an online store or free email service where a database of users or customers was leaked in the past and found on the internet. The attacker has no access to your computer or webcam.
- If you use "the same password everywhere" (for email, work computers, home computers, e-shops, online banking), and the extortionist used that password in the email, it’s time to set different, strong passwords for all accounts.
Inheritance, Stolen Money
Also known as “Nigerian Letters.” The scammer entices the victim with the promise of a large sum of money. For example:
-
A fabulously rich Sheikh Novák has died, and a desperate lawyer is looking for an heir. Since there are few Nováks in the Sahara, the lawyer has started looking in the Czech Republic and is sure that you are the one.
-
A billionaire is dying and wants to donate his fortune to charity, but needs someone to organize it. He found you online, and you can keep a nice commission.
-
A widow of an American general has fallen in love with you. Though you would need to move to Nigeria, since the late husband hid a few million dollars, you would live like royalty.
If you encounter this:
Ignore it.
If the victim replies and starts corresponding with the scammer, they will never receive any money. On the contrary, the scammer will extract money from the victim ("I need $100 for banking fees - what’s that compared to the promised millions"). If the victim doesn't have the money, listen to this report by Czech Radio about a pensioner from Šumava, who is serving time in Hong Kong for drug trafficking.
And Finally:
- Be cautious, no technical protection is 100% effective
- If you are unsure, ask
- It’s human to make mistakes, but hiding mistakes can cause great harm





















